Mobile technologies have come a long way since the nascent days of the 1980s. In the early years, we had simple two-way pagers and clunky mobile phones the size of landline headsets, and poor reception only available within limited radiuses. Mobile technologies are now ubiquitous with high tech gadgets that work in the remotest of places.
Table of Contents
ToggleToday, a standard mobile device isn’t merely a unit for verbal and written communication; it also works as a GPS navigation device, Internet browser, and gaming console. Also, through mobile apps, functionality is extendable to a whole range of capabilities.
What Is Mobile Technology?
Mobile technology refers to any technology that’s “portable.” The critical components of mobile technology are as follows:
- Portable 2-way communication devices
- Cellular technology or networking technology
Different Types of Mobile Technologies
What are the different mobile technologies? There are four main types of mobile networks – cellular communication, 4G networking, Wi-Fi, and Bluetooth connections. Below is an in-depth analysis of the different types of mobile technologies.
Cellular Technology
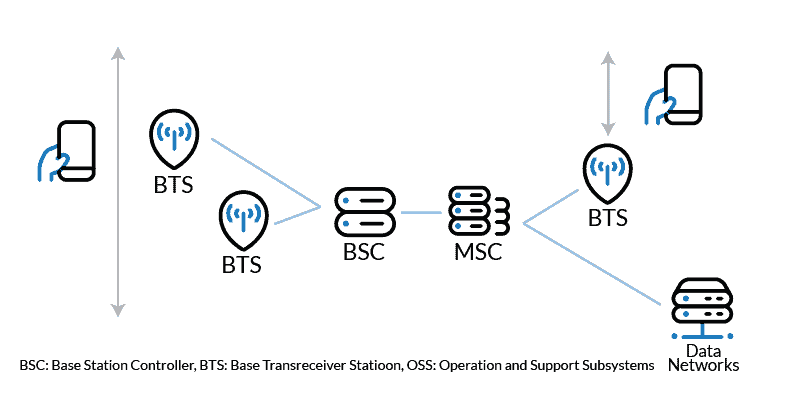
The first on our list of mobile technologies is cellular technology. A cellular network is a communication system where the last link is wireless. Mobile signals travel from the transmitting device and onto a mobile base station.
The base station transmits the signal to a switching center, and from here, it is sent over other base stations until it reaches the receiving device.
Cellular companies have to calculate the required number of base stations needed within a service area. To achieve the same transmission quality in all coverage regions demands that all the areas be of uniform shape and size.
The most common model used for mobile networks is uniform hexagonal-shaped regions, called cells – hence the term “cellular technology.” The image example below shows a base station with an omnidirectional antenna constructed in each cell’s center.
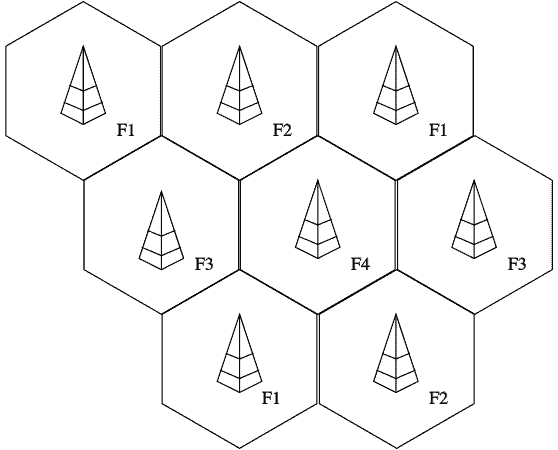
These cells provide broad geographical coverage and enable many different types of portable devices to communicate with each other and with other fixed devices connected to the network.
To make a phone call or browse the Internet with a mobile device, the device connects to a base station as a first step. A cellular network consists of thousands of base stations, and most of the earth’s populated land area is covered by base stations.
The mobile device must select the base station that offers the best service quality. This association is one of the fundamental radio resource management problems.
When a user is on the move, the mobile device must keep changing the association because each base station has limited coverage – this is known as handover.
The other radio resource problem is that multiple devices need to communicate simultaneously and share capacity over the same channel. The solution to this problem is a medium access control (MAC) protocol.
An MAC protocol multiplexes several data streams of different devices to share the same channel and deal with addressing issues – how a device obtains a channel when it needs one, and so forth.
MAC protocols were originally designed for wired communications where several computers needed to transmit data packets simultaneously in a local area network (LAN).
The physical media in wired networks is copper or fiber optic cables, which are reliable and have abundant bandwidth. There is little packet loss, and the MAC protocol designs are relatively simple.
In mobile networks, the MAC protocol designs are complicated mainly due to diffraction, scattering, or reflection of a radio signal as it reaches its receiver. In such cases, the signal deteriorates, the signal quality varies, and robust transmission is needed to mitigate the issue.
There is also substantial interference from other nearby mobile devices. There are two types of MAC protocols, contention-free and contention-based.
Contention-Free
In this design, a central controller coordinates resource allocation. The central controller may be a base station in a cellular network or an access point in a wireless local area network.
Pre-determined or assigned network resources such as antennas, frequency bands, codes, and time slots are used by devices to send data packets.
A central scheduler ensures that the transmissions of different devices do not conflict. Network providers can guarantee the quality of service (QOS) for this protocol design.
Contention-free access protocols use five basic partitioning techniques as follows:
- Frequency division multiple access (FDMA): This is the oldest partitioning method. Multiple channels communicate with the base station. A link is allocated in a single session, a frequency band distinct from other links. The corresponding receiving device can tune to the desired band and received data packets without conflict. When a channel is not in use, it lies idle and can’t be used by other users. Every device transmits simultaneously and continuously on the assigned channel. This partitioning technique is typically found in narrowband systems. However, it is inefficient at handling traffic flows that exhibit different bit rate requirements.
- Time-division multiple access (TDMA): This is a more flexible partitioning technique when managing applications with varying rate requirements. With static TDMA allocation, all terminals are synchronized, and time is divided into discrete slots such that only one link is active at a time. For example, if two mobile devices communicate with the base station and have the same rate requirement, one device is assigned even time slots and the other odd time slots. When there are multiple devices on the network, complex scheduling algorithms are deployed. Also, in TDMA, data packet transmission is not continuous (streaming) – buffering happens first, and transmission then occurs in bursts. Additionally, devices do not require simultaneous communication in both directions because the time slots used for transmission and reception are different. The allocation of varying time slot numbers per frame to different devices allows resource allocation to devices based on demand.
- Spread-spectrum multiple access (SSMA): This is a class of channel partitioning techniques combining frequency and time multiplexing. Signals have a bigger bandwidth than the information data rate. Frequency Hopping (FH) systems and Direct Sequence (DS) are the most popular techniques in this class. Frequency Hopping Code Division Multiple Access (FH-CDMA) combines time and frequency multiple access techniques. It is similar to the conventional FDMA systems, but users hop from frequency to frequency, and each device has a unique hop sequence. This way, interference is averaged out. Direct Sequence-Code Division Multiple Access (DS-CDMA) uses a technology known as direct-sequence spread-spectrum modulation. Unlike TDMA and FDMA, spread signals from different devices interfere with each other unless all users’ transmissions are flawlessly synchronized, and orthogonal spreading codes are used.
- Orthogonal frequency division multiple access (OFDMA): OFDMA is based on orthogonal frequency division multiplexing (OFDM). OFDM uses orthogonal subcarriers to send numerous data symbols in parallel mode and achieves high spectral efficiency. OFDM is very simple to implement and is robust against multipath fading and inter-symbol interference. Also, OFDM has low sensitivity to time synchronization errors. On the other hand, OFDM is very sensitive to frequency-domain errors such as Doppler shift and frequency synchronization problems.
- Space division multiple access (SDMA): Mobile devices are usually positioned far away, and SDMA uses this spatial separation to reuse the frequency spectrum for higher network capacity. The simplest method of SDMA is reusing the same frequency in different cells of a mobile cellular network. To guarantee satisfactory co-channel interference, the cells that reuse the same frequency are adequately separated in space. A more advanced SDMA technology facilitates frequency reuse within each cell. This technology uses smart antenna arrays and intelligent signal processing methods to point the antenna beam to the desired users and places. It cancels out in the direction of other devices.
Hybrid models combining these methods are also used to partition channels to achieve further performance improvement.

Contention-Based Mobile Technology
This design allows devices to access the wireless medium at random when they need to transmit data. Lack of coordination leads to inevitable packet collision.
The MAC protocol design is devised to minimize collisions. This protocol is easier to implement and performs well when traffic is light, but there is considerable performance degradation when traffic is heavy.
Contention-based access protocols use two main partitioning techniques as follows:
- ALOHA: This protocol was first developed at the University of Hawaii and utilized in a VHF radio system in the 1960s. The ALOHA algorithm is quite simple.
- Step 1: If there is a message to send, send it
- Step 2: If the transmission succeeds, remove the message from the queue
- Step 3. If the transmission fails, wait for a random time interval, i.e., backoff randomly, and go to Step 1
Collisions are the leading cause of transmission failures. The mobile devices mustn’t wait for identical time intervals if a collision occurs because this is highly likely to lead to another collision.
To avoid this, all mobile devices perform a backoff scheme and decide randomly when to attempt the transmit. The efficiency and network capacity of this protocol are dependent on the quality of the backoff scheme.
- Carrier Sense Multiple Access (CSMA): This protocol solves wasted bandwidth and energy once data packets start colliding. CSMA is prevalent in asynchronous wireless networks with low distribution delays. Each device is outfitted with a receiver to “listen” for ongoing transmission in the channel. The devices only measure the signal level to detect transmission – this is known as carrier sensing. If there is a transmission in progress, the device halts its transmission attempt and retries later. After a data packet is transmitted, the terminal listens for an acknowledgment. If none is forthcoming, the packet transmission is rescheduled. Mobile networks also use CSMA as carrier sense multiple access with collision avoidance (CSMA/CA). In this technique, collisions are avoided. A terminal with a message to transmit will sense the channel first. If the channel is idle for a short period called the DIFS (DCF inter-frame space, where DCF is the distributed coordinated function) period, the device can transmit. Otherwise, the device will defer and continue monitoring the channel until it is idle for the DIFS period. Then, a random backoff counter within the contention window is generated before actually sending the message. The backoff counter counts down as long as the channel remains idle. The counter will pause if the device detects the channel busy and resume after detecting the channel is inactive for another DIFS period. The device will transmit immediately when its backoff counter is zero.
Data Traffic Performance Measures
There are three mobile data traffic performance measures as follows:
- Delay: This measure refers to the time it takes to transmit a message and the round-trip time a round-trip takes to receive an acknowledgment.
- Delivery Performance: This metric examines the quality of the transmission, and there are two ways to assess quality. The first method is known as the Residual error probability (REP) and is the likelihood that the message received contains errors. REP is measured using the Bit Error Rate (BER), a percentage computed by taking the number of bits in error and dividing by the total number of transferred bits during a specific time. The second method to assess delivery performance is examining the Packet Error Rate (PER). PER is the ratio of the number of packets not received to the number of packets transmitted.
- Throughput: The individual throughput of a device is the expected number of messages successfully transmitted by a device and received by the receiver within a specified time.
4G Networking
To understand 4G technology, one must first understand the history of mobile technology.
History of Mobile Technology
The history of mobile phone and mobile technology can be said to have begun with the first generation of wireless mobile technologies.
1G (First Generation)
1G was the first generation of wireless mobile technologies. The mobile technologies that characterized this era included:
- ETACS (European Total Access Communication System)
- NMT (Nordic Mobile Telephony)
- TACS (Total Access Communication System)
1G used the analog system and signals. The drawback with analog signals is that they can’t cover a long distance.
Second Generation
- 2G: This marked the beginning of the digital era and was characterized by the following wireless mobile technologies:
- GSM: Its original name was Groupe Special Module, but after it became the global standard, the name changed to Global System for Mobile Communication. This mobile technology is credited with making voice communication over long distances ubiquitous.
- WCDMA: Wide Band Code Division Mobile Access also developed concurrently with GSM and was used in many countries such as the United States.
- 5G: Better known as GPRS, which is an abbreviation for General Packet Radio Service. This technology marked the beginning of Internet connections through mobile devices. Unfortunately, the data transfer rate is very slow.
- 75G: This wireless mobile technology is also known as EDGE, an abbreviation for Enhanced Data Rates for GSM Evolution. As the name suggests, this mobile technology improved data transfer rates and thus offered faster Internet connections. This technology is still supported by many carriers around the world and is found on feature phones.
Third Generation
- 3G: The need for faster data rates and greater capabilities led to the development of 3G. 3G is also known as UMTS, which stands for Universal Mobile Terrestrial/Telecommunications System. It offered a data rate of 384Kbps, whereas Edge could only manage 170Kbps, and 56 to 64Kbps for GPRS. These new speeds made services like video calling and streaming services possible.
- 5G: This mobile technology is also known as HSDPA (High-Speed Downlink Packet Access). This improved the download speeds based on the fact that Internet traffic is asynchronous with higher download demand at any given time. But, during this era, cloud computing took off, so there was a need to improve upload speeds. Thus, HSUPA (High-Speed Uplink Packet Access) mobile technology was developed. Both HSDPA and HSUPA offered speeds of 2Mbps.
- 75G: The next development was HSDPA+. The plus sign represents increased speeds.
4G (Fourth Generation)
The first release of 4G was sometimes referred to as 3.9G or LTE (Long-Term Revolution). It was first launched in Oslo in 1998 before being adopted around the world.
4G is the current de facto mobile technology in use in most places around the world. The 4G standards specified by the International Telecommunications Union-Radio communications sector (ITU-R) set Internet speed requirements of 1Gbps for stationary users and low mobility communication and 100Gbps for high mobility communication such as while traveling in a vehicle or train.
5G
5G is the latest mobile technology, and deployment in some parts of the world began in 2019. Speeds will range from 50 Mbps to 10Mbps. 5G is a breakthrough new cellular phone technology needed to facilitate the development of the Internet of Things (IoT) technologies. The increased bandwidth also effectively competes with cable Internet.

Wi-Fi
The next type of wireless mobile technology is Wi-Fi, which is highly popular. According to recent data, Wi-Fi enabled devices reached 3.05 billion units in 2019.
The non-profit Wi-Fi Alliance trademarked the term “Wi-Fi.” The use of the name is limited to branding certified products tested for interoperability.
Wi-Fi certified devices connect to LAN Internet routers or access points and use the wired (Ethernet) connection for data transfer. Therefore, Wi-Fi makes it possible for 3G and 4G devices to access the Internet at speeds that aren’t possible using cellular data networks. Users connect to a Wi-Fi network by selecting the network name (SSID) and entering the password.
Wi-Fi is a family of wireless network communication protocols based on the IEEE 802.11 local area network (LAN) protocols – one of the world’s most pervasive wireless computer networking standards.
Below is a breakdown of some 802.11 protocols:
- 11a: 802.11-1997 was the first protocol but is now obsolete. It was replaced in 1999 by 802.11a. This protocol has theoretical speeds of 54Mbps. This technology wasn’t popular because it ran on 5Ghz frequency, which has poor range. Indoors it could only average 25ft of coverage.
- 11b: This technology was popular and took off because it was affordable and had an indoor range of up to 100ft. Unfortunately, greater range came with low speeds at only 11Mbps. The slow speed was because it ran on a 2.4Ghz frequency.
- 11g: This marked the period when Wi-Fi got good enough for widespread adaptability. This protocol had the speed of 802.11a and the range of 802.11b running on 2.4Ghz frequency. This feature also meant it was backward compatible with 802.11b for devices designed to run on 802.11b. However, 802.11b devices could not achieve the new speeds.
- 11n: The speed jump was huge from 54Mbps; this new protocol offered speeds of between 300 and 600Mbps. Multiple Input Multiple Output (MIMO) technology also made it possible for multiple devices to connect to a single access point. It runs on both 2.4 and 5Ghz frequencies. This feature allows users to select optimum configurations for range and speed for their connections.
- 11ac: This was published in 2013 and quickly evolved into the preferred standard. It came with wider frequency channels in the 5Ghz band, which led to huge increases in the speed of between 400Mbps and 1Gbps. It only runs on the 5GHz frequency band. Also, improved MIMO technology meant that even greater numbers of devices could connect to routers with less signal conflict. Beamforming also allows the access point to directly send a signal to a device, further improving it.
- 11ax: It has become prevalent since its launch in 2019. The naming conventions have also changed. The Wi-Fi Alliance has marketed this as Wi-Fi 6. The theoretical speeds are 3.4 to 15Gbps on multiple combined streams. This Wi-Fi protocol uses contention-free Orthogonal frequency division multiple access (OFDMA) channel partitioning to handle numerous devices’ connections. This multiplexing technique allows vast numbers of devices to connect to the same access point without any signal deterioration. It is an excellent development for the future of IoT. Wi-Fi 6 uses both 2.4 and 5GHz, frequency bands. This feature makes it backward compatible with all early devices though the speed will remain capped at the device’s speed limitations. Multi-user MIMO has also been implemented, which reduces interference and increases throughput. It also has a new feature known as Target Wakeup Time (TWT), which reduces battery drain on mobile devices.

Bluetooth
This mobile technology is a telecommunications industry standard to connect computing devices over short distances. With Bluetooth technology, users can quickly pair devices such as headsets and speakers with desktops, laptops, and phones.
Some key benefits of Bluetooth technology include:
- Cable replacement: Bluetooth eliminates the need for cable connections between mobile devices and accessories such as headphones and speakers.
- Cost savings: Bluetooth technology is low energy.
- Easy file sharing: An Internet connection is not necessary to share files between mobile devices.
- Internet connectivity: Mobile devices can use Bluetooth to tether the Internet connection to other devices.
An electronic conversation occurs when Bluetooth is activated on a device and comes within range of another Bluetooth activated device. The devices either have data to share or one device needs to control the other.
Once the conversation initiates, the devices form a network.
Every Bluetooth device has a transmitter and a receiver. The device transmitters’ power determines the maximum range over which Bluetooth connectivity is possible. Devices fall under one of three classes as follows:
- Class 1: These devices have a maximum output power of 20Dbm and 100Mw. Their range is 100 meters. Sample devices include USB adapters and Access Points.
- Class 2: These devices have a maximum output power of 4Dbm and 2.2Mw. Their range is 10 meters. Sample devices include mobile phones, Bluetooth adapters, earphones, headphones, and smart card readers.
- Class 3: These devices have a maximum output power of 0Dbm and 1Mw. Their range is 1 meter. Sample devices include Bluetooth adapters.
There are two types of network topologies:
- Piconet: A single Piconet is formed by one master device and one slave device. A multiple Piconet is created by one master device and several slave devices. The master device initiates communication with other devices and dictates the transmissions of a slave device. Slave devices cannot communicate with each other in a Piconet. The maximum number of active slaves in a Piconet is seven or eight devices when you include the master.
- Scatternet: This is a combination of several Piconets. A master in one Piconet can be a slave in another Piconet.
As with other mobile technologies, Bluetooth technology uses frequency bands. They exchange data in the ISM (Industrial, Scientific, and Medical) band of 2.4GHz.
The spectrum begins at 2402MHz and ends at 2483.5MHz. It consists of 79 channels, each having a 1MHz bandwidth. It uses the contention-free Spread-Spectrum Multiple Access (SSMA) frequency hopping technique to reduce transmission interference and reduce eavesdropping.
Use of Mobile Technologies
What is mobile technologies used for? The development of mobile technology opened a plethora of business and personal uses. The benefits of mobile technologies run the gamut from simple things like communicating while away from the office to complicated stuff like sending money and monitoring your health vitals.
What follows is a breakdown of the use of mobile technologies and the benefits of mobile technology.
Mobile Technology – Communications
What is the most important use of your cell phones? You would most likely say you use it most for voice communication. Many young people born after mobile communications become widespread do not appreciate how difficult it was in the pre-mobile days.
Families could not keep in touch once they left the household – and for businesses, it was challenging to get updates from staff in the field. Information moved slowly, and this constrained commerce.
Today, mobile communication isn’t limited merely to voice communication. We have SMS, chat, video, and Internet applications. In addition to communication via voice while away from the office, people can send and receive emails.
Remote working is now touted as the future of work for most white-collar occupations due to mobile communications development. Examples of mobile technology making this possible include video calling applications such as Zoom and Skype, and collaboration and task management tools such as Trello and Hubstaff.

Mobile Technology – Commerce
Mobile commerce, the buying and selling of goods through mobile devices, has completely changed global trade. eCommerce over mobile gadgets has spawned a wide range of products and services. Examples of mobile technology in this space include:
- Mobile money transfer: Nowhere has mobile commerce been more disruptive than in the area of mobile money transfer. In March 2007, Safaricom, a Vodafone subsidiary in Kenya, was the first company to develop and successfully deploy the first mobile money transfer network dubbed Mpesa. The innovation allowed a user to send money from a mobile wallet to another user. The receiver can use the funds to pay for goods and services at participating outlets or withdraw the cash from Mpesa agent kiosks. Users can also deposit and withdraw funds into their bank accounts. By May 2019, Mpesa had 22.6 million active users and over 167,000 agents. Mpesa also accounted for 2% of the company’s revenue and made a $634 million net income. The technology has been successfully replicated worldwide, especially in low-income countries in Africa, Asia, and Latin America, where there is low banking penetration.
- Mobile ticketing: Ticketing for events and public transport is now mainly done through mobile ticketing services. Users receive the ticket in the form of an image and display it when they check-in.
- Mobile vouchers, coupons, and loyalty cards: These are now also primarily distributed via mobile devices. This has increased their portability, durability and led to platforms where they are bought and sold.
- Content purchase and delivery: In addition to digital content being delivered wirelessly to PCs and laptops, digital content is now delivered to mobile apps and devices.
- Location-based services: The location feature in mobile devices led to several services. Chief among these is the ability to send you notifications of product offers and discounts in a specific geographic area. Weather reports are also a spinoff of location services. Businesses can also track the movement of staff and deliveries using location apps. The online taxi industry would not have been possible without location-based technology.
- Information services: Gone are the days when you needed to buy a newspaper to get your daily diet of world news, stocks, politics, sports, gossip…you name it. Information is delivered to mobile devices every second.
- Mobile banking: Banks have mobile applications that customers use to operate their accounts without stepping into a branch.
- Mobile brokerage: Stocks, bonds, and financial instruments are now traded from mobile applications.
- In-application mobile phone payments: In-app mobile phone payments, where users pay for additional features or functionality while using an application, are expected to be bullish over the next decade.
- Mobile marketing and advertising: In the context of mobile technologies, mobile marketing and advertising runs exclusively on mobile devices. In the nascent days of mobile advertising, companies did not think it was worth the ad spend. There was also a technical problem with designing ads that displayed well on small screens. But after it became apparent that mobile advertising had greater reach than traditional broadcast advertising, marketers began shifting more ad budget to mobile marketing. Today, Google and Facebook earn more revenue from mobile advertising than other channels.
Mobile Technology – Wearables
Wearables are revolutionizing the Health and Personal Care Industries. They come in many forms, including headgear, straps, shirts, wrist-worn, belt clips, and shoe-worn or foot pods.
Sports companies initially developed them, but now Internet companies and tech startups are in on the action. Wearables allow us to gain much biometric information about our bodies and leverage this data to live healthier, happier lives.
Knitting machines are now configured to weave the biometric technology right into textiles so that we now also have smart apparel.
Mobile Technology – Learning
There are five main ways mobile technologies are used to improve learning efficiency and effectiveness.
- Audio recording: College students use mobile devices to record lectures and play them back later. Listening to audio recordings after learning sessions is one way to improve knowledge retention. Instructors also provide feedback via audio recordings.
- Live polls: Quizzes via online forms are administered at the beginning of sessions to ascertain knowledge gaps. Polling in this manner ensures that instructors focus on these areas. At the end of the learning session, exit polls check if students have learned.
- Video creation: Instructors ask students to create short videos of what they have learned after a reading assignment. This teaching methodology has virtually eliminated plagiarism because making a video demands that the student intensely understands the content.
- Chats and forum discussions: Instructors worldwide extensively used this feature of mobile technologies during the COVID-19 pandemic. Learners and instructors use mobile devices to participate in online chats and forum discussions on content topics.
- QR codes: Quick Response codes in content are quick and easy to add references to further reading material.
- Voice recognition and speech to text: Dyslexic students and students with other learning disabilities benefit greatly from voice recognition and speech synthesis mobile applications.
Pros and Cons of Mobile Technology
Mobile technologies have benefited society. But, as with every technology, there are also some drawbacks. Let’s now consider some of the pros and cons of mobile technology.
Pros of Mobile Technology
It goes without saying that the pros outweigh the cons. Some of the most apparent advantages of mobile technology include:
Efficiency and Productivity
Mobile technologies have infused efficiency and productivity in many spheres of life and business. The examples are just too many to cite. But the most significant benefit is communication.
Mobile technologies have allowed instant remote communication via various methods – voice, video, chat, and Internet applications.
Quality and Flexibility of Service
Mobile technologies have improved the quality and flexibility of services in many industries. Customers have a more comprehensive range of shopping options, purchasing methods, fulfillment, and delivery, thanks to mobile technologies.
Many industries have been completely disrupted by mobile technologies giving rise to new tech companies that build technology to run an ecosystem without providing the service. The best example is online taxi services, such as Uber, Bolt, and Lyft.
Wireless Payments
Mobile technologies have made it possible to pay for goods and services with a simple tap from your mobile device. Examples of leading technologies in this space include direct carrier billing, Internet payments via a mobile browser, Magnetic Secure Transmission (MST) payments, Mobile banking, mobile wallets, Near Field Communication (NFC) payments, payment links, quick response (QR) code payments, and SMS payments.
Improved Networking and Computing Capabilities
Mobile technologies typically provide last-mile connectivity. This feature has made Internet connectivity and mobile computing ubiquitous. Without this connectivity, many mobile solutions and services would not be possible.
Human Rights and Access to Information
Perhaps one of the most significant benefits of mobile technologies is improved access to information for all people worldwide. There are two principles concerning information access.
The first is the legal principle of Freedom of Information – the idea that all citizens in a country have a right to access public bodies’ information.
The second principle is that lack of access to technology often hinders access to human rights knowledge and general information about how the world works and how to find solutions to everyday problems.
The Internet’s development closed the knowledge gap by making all kinds of information available to anyone with a computer and Internet access. But true universal access to information was made possible by mobile technologies.
With a simple Internet-enabled feature phone costing less than $10, anyone can log onto the Internet from most parts of the world and search for information on any kind of topic. However, mobile technologies can also disrupt human rights, as explained below.
Cons of Mobile Technology
Let’s now consider some disadvantages of mobile technology.
Disruption of Human Rights
While mobile technologies have made it possible for people with the technology to access information more easily, they also disrupt human rights when people don’t have access to the technology.
According to recent data, about 4.66 billion people were active Internet users as of October 2020, amounting to 59 percent of the global population.
And, while mobile is the most important channel for Internet access worldwide, accounting for 91 percent of total Internet users, there are still over 3 billion people on the planet who don’t use the Internet actively.
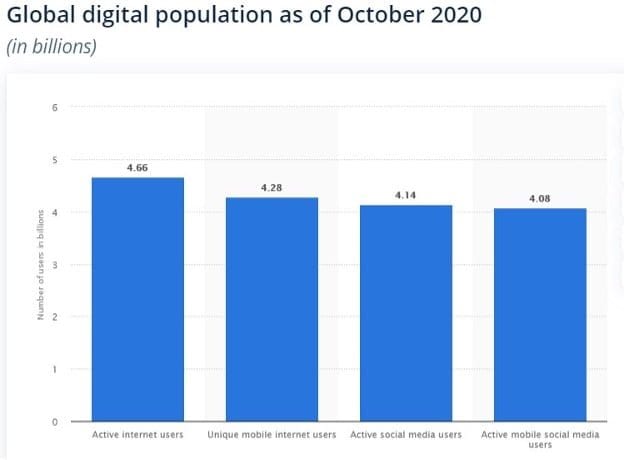
This digital divide is caused by global inequality. And, it isn’t just limited to third world countries. According to a Pew Research Center Study, 10% of Americans, over 30 million people, have no access to the Internet.
Repressive governments have also caught on and become more adept at using technology to censor and restrict access to information. The best example is the Great Firewall of China, highly advanced censorship, tracking, and espionage technology deployed by the Chinese government on a massive scale to prevent its citizens from accessing and disseminating information.
Governments have committed human rights violations on a large scale in the name of security. In 2013, Edward Snowden leaked millions of documents to journalists about the US Government’s illegal espionage program on its citizens and foreign citizens.
Distraction
Unfortunately, mobile technology is distracting at work and in our personal lives. At work, lots of working hours are wasted as people browse social media during working hours.
Students also get distracted by social media and the Internet. Mobile technology has also led to accidents and loss of life when people are too distracted to notice what is happening around them.
Otis Johnson, a convict released from prison in 2014 after serving a prison term of 44 years, narrates in a video interview how he encountered strange behavior at Times Square New York, of people walking while their eyes were glued to their mobile devices.
He couldn’t help but wonder how they could tell where they were going. It may sound comical, but such an observation by someone who was practically an alien to the modern world is instructive of mobile technology’s distracting power.

Training and Equipment Costs
While mobile technologies have been beneficial in many aspects, individuals must know how to use them to reap the maximum benefits. This isn’t a significant problem for personal areas since most mobile devices and applications are intuitive enough for an 8-year old to figure out.
The main problem is with business applications. Companies deploying a new mobile application must invest time and resources to train staff. This added cost makes the playing field uneven.
Smaller companies with limited training budgets to get in on the action fast enough can’t, therefore, compete effectively. The same goes for the actual mobile devices needed to implement mobile computing and solutions – mobile devices aren’t cheap. An Apple iPad Pro retails at over $700.
For small and medium-sized businesses that want to transition to mobile computing fully, the cost is prohibitive.
Privacy Concerns
Mobile technologies lead to privacy concerns. We have already discussed governments’ espionage and censorship actions, but there are also commercial entities’ activities.
Every single mobile application on your device collects data about you. While laws make it mandatory to anonymize the data so that it doesn’t identify individuals, advanced artificial intelligence methods can examine data and accurately infer social status, political orientation, sexual orientation, religion, and other facts about an individual.
Many mobile app companies also sell information to third-parties. This information is used to send targeted ads. The jury is still out on the ethics of this practice.
Still, it’s quite uncanny to have an advertisement about shoes follow you around everywhere you browse simply because you like a shoe company’s page on Facebook.
Health Concerns
Finally, we would be remiss if we failed to address some health concerns. Specifically, what are the negative effects of smartphones?
“Is mobile harmful for brain?” is a popular Internet search. But, are phones bad for your brain? Well, let’s consider what science has to say.
According to the World Health Organization (WHO), mobile phone radiation is possibly carcinogenic. This classification means your smartphone is likely to cause cancer when used for prolonged periods daily over many years.
WHO has published exposure limit guidelines for workers who need to use smartphones for extended periods.
However, while cell radiation is classified as possibly carcinogenic, no studies prove a direct link between smartphones and brain cancer. A large scale study in Denmark found no association between cell phone use and brain cancer.
Why Is Mobile Computing Important?
Mobile computing refers to a computing environment over the physical environment. In other words, computing occurs while a user is mobile by carrying around the computing device.
Mobile computing involves mobile devices and other hardware, mobile software, and mobile communication systems.
There are several reasons why mobile computing is important. They include:
- Availability: The portability of mobile computing makes it available on-the-go anywhere and at any time.
- Location flexibility: The use of portable devices allows employees to continue their work regardless of the location. Workers can work at home, on factory floors, warehouses, inside mines, and in just about any hospitable environment.
- Increased productivity: Since mobile computing is always available, Internet applications have parallel mobile applications that improve productivity. For example, Quickbooks accounting software is an Internet application that has a mobile version.
- Cost-effective: The importance of mobile technology is also evident in costs. For example, in the wake of COVID-19, many white-collar workers are working from home. Remote working would not be possible without mobile computing. So, mobile computing allows people to work from home regardless of company location and infrastructure –companies where staff predominantly work from home save on rent, utilities, and other staff-related costs.
However, mobile computing also has a few issues, including:
- Connectivity: Mobile computing is ineffective in the absence of robust wireless connectivity. Good quality connectivity is necessary for communication, collaboration, and cloud computing.
- Power consumption: The power needed by mobile base stations and Wi-Fi access points to send signals to mobile devices is directly proportional to the distance. This high-power consumption means that as commerce transitions more to mobile computing, power companies must find cheaper and cleaner electricity sources. Additionally, mobile devices need to be charged continuously, so mobile computing is impractical when charging points are not nearby.
- Security concerns: Wireless networks are prone to attack and eavesdropping. Security companies are continually fixing loopholes, but criminals keep finding kinks in the armor. We also mentioned how governments around the world conduct espionage on their citizens, as do private companies.
Future Cell Phone Technologies
Let’s conclude by looking at what future cell phone technologies might look like and the best upcoming future cell phone technology.
There is no doubt that 5G is the future cell phone technology. There are dozens of connectivity problems that plague us using 4G and inferior technologies – for example, poor network coverage due to interference and distance, mobile device download speeds, lagging video calls, to mention a few.
According to the International Telecommunications Union (ITU) standards, a single 5G cell must have a theoretical speed of 20Gbps. To put this in perspective, a 100 Gb 4K movie would take a mere 5 seconds to download it on 5G.
Latency, a delay before the device processes what it is supposed to do, is another major problem with 4G networks. The current latency for a video chat on 4G is about ten milliseconds in places with good coverage.
In areas with inadequate coverage, the latency is much worse. On 5G, the latency is one millisecond, a tenth of the best scenario with 4G.
Connection density, the number of devices that can connect to the network without it crashing or slowing down, on 4G is about 5,000 devices per square mile. On 5G, it is 2 million devices per square mile. This feature eliminates any network problems in high population areas.
5G doesn’t just stop at network quality improvements. It opens up a whole new world of possibilities in the new and emerging tech sectors such as the Internet of Things (IoT), autonomous vehicles, and smart homes.
With IoT, Internet-enabled devices will be able to connect, interact, and improve our quality of life. Much of the stuff that we see in science fiction movies could soon become a reality.
Self-driving cars will rely heavily on the connectivity that 5G will provide. An autonomous vehicle has a light detection and radar, a GPS positioning system, video cameras, and a central computer to process all this data.
In health, 5G will make it possible for doctors to perform remote surgeries using robot arms. A surgeon in China has already provided proof of concept by performing remote surgery on a lab animal.
People Also Asked
What is an Example of Mobile Technology?
Wi-Fi is an example of mobile technology. It gives Internet-enabled mobile device users access to fast ethernet via an SSID (Network name) and password.
What are the Types of Mobile Technology?
There are several types of mobile technology, namely cellular technology, 4G technology (including all generations), Wi-Fi, and Bluetooth.
How Many Types of Mobile Devices Are There?
A mobile device is any portable computing device. Examples include; laptops, tablet computers, smartphones, and other handheld gadgets.
What is the Advantage and Disadvantage of Mobile?
There are many advantages of mobile technology. The main benefits are the ubiquity of human communication and access to information. The main disadvantage is the privacy concerns that come with the widespread use of mobile.
Are Mobile Phones Good or Bad?
It depends on whom you ask. Repressive regimes censor mobile communications because access to information leads to greater demand for human rights and action against violations. Mobile phones have done more good than harm in the world.
What is the Latest Technology in Mobile Phones?
The latest technology in mobile phones is 5G technology, which will deliver ethernet-like speeds on mobile devices and open up a whole new world of possibilities.
Which company is the best for mobile?
The answer depends on your location. The typical setup is that each area has a dominant provider or a few dominant providers that provide the best quality of service.
What is the latest IT technology?
IT technology is a fast-evolving space. Bleeding edge tech today may be obsolete tomorrow.
What is the Future of Mobile Technologies?
Several technologies will determine the future of mobile technologies. Key among these is the adoption of 5G technology. 5G will lead to the true ubiquity of mobile.
What is Mobile Technology Used For?
Mobile technology is used for communication, commerce, wearables, learning, health, and many other facets of life.
How Does Mobile Technology Affect Our Lives?
The impact of mobile technology has mostly been positive on human lives. Mobile technology has improved communication, facilitated commerce, improved learning and health outcomes, and impacted our lives in numerous ways.
What Are The Best Uses of Mobile Technology?
The best use of mobile technology is in mobile communications and commerce. These are the two areas where there have been great solutions.
What is the Future of Mobile Technology?
The future of mobile technology is 5G. 5G technology opens up new frontiers of mobile technology and makes theoretical IoT applications possible.
What are the Negative Effects of Smartphones?
Smartphones have a few adverse effects, such as distraction leading to physical injury and low productivity.
Is Mobile Harmful For Brain?
There is no definitive research that concludes that mobile is harmful to the brain.
Are Phones Bad For Your Brain?
Phones are not bad for your brain. However, the World Health Organization has classified cell phone radiation as possibly carcinogenic with prolonged use over many years.
What Diseases Are Caused by Mobile Phones?
There are no known diseases that are caused by mobile phones.
What is Mobile Technology in Education?
Mobile technology in education refers to the use of mobile technologies to improve learning outcomes.
What Are the Types of Mobile Technologies?
There are several types of mobile technologies; cellular technology, 3G, 4G, 5G, Wi-Fi, and Bluetooth.
Which Language is Used in Mobile Phones?
Android and iOS are the two dominant mobile platforms. Java is the official programming language for Android development, while Swift is the official programming language for iOS and OS X development.
What is Meant by Mobile Technology?
Mobile technology refers to tech that runs on portable Internet-enabled devices.
What is the Latest Mobile Technology?
There is no definitive answer to this question. The latest mobile technology today may be old news tomorrow.







