Recent events like the Cambridge Analytica scandal and the introduction of the European Union’s General Data Protection Regulation (GDPR) have thrown the spotlight on issues concerning the protection of personal information online.
Table of Contents
ToggleWith the GDPR now in force, consumers and internet users originating from or based in the European Union (EU) now have a greater measure of privacy protection and control over how commercial organizations and data collectors/processors access their personal information – online, and through a range of other methods on the ground.
Privacy and data-handling laws in many other parts of the world have been amended to keep pace, and to give companies in those areas that do business with the EU a better chance of remaining competitive.
But there are regions where the legal system falls short in protecting citizens. And even the strongest laws can’t protect people from their own careless practices, or the malicious activities of hackers and information thieves who are truly dedicated to their craft.
So, how can you actively protect your personal information online? We have some recommendations.
Don’t Give Out Your Details to Just Anyone
Sounds like a no-brainer, but the age-old parental advice that you should “Never talk to strangers” also applies in the digital world. If an unknown website, email correspondent, or service is asking for sensitive details about you, a straight up refusal should be your instinctive reaction. If there’s a pressing reason to deal with the entity, do a thorough search to check them out before revealing any of your personal information online.
Likewise, don’t give out your email address or mobile phone number like you’re distributing party favors. You might never know who the person or organization that gets hold of it is connected to.
Get Smart and Complex with Your Passwords
Security experts continuously stress the importance of maintaining good password habits. Strong passwords consisting of eight or more characters with a mix of numbers, letters, and keyboard symbols are always advised. With numerical PINs (Personal Identification Numbers) and passcodes, there may be a limit to the number of characters you can use – but you should still endeavor to make your unique codes as complex and un-guessable as you can.
Don’t use logical variations of the same password (e.g., MyName01, MyName02) across multiple sites. Even if the combinations aren’t that easy to guess, if a determined hacker does manage to figure one out and decides to try out a few permutations, they might be able to access your other accounts and seriously compromise your business data or personal information online.
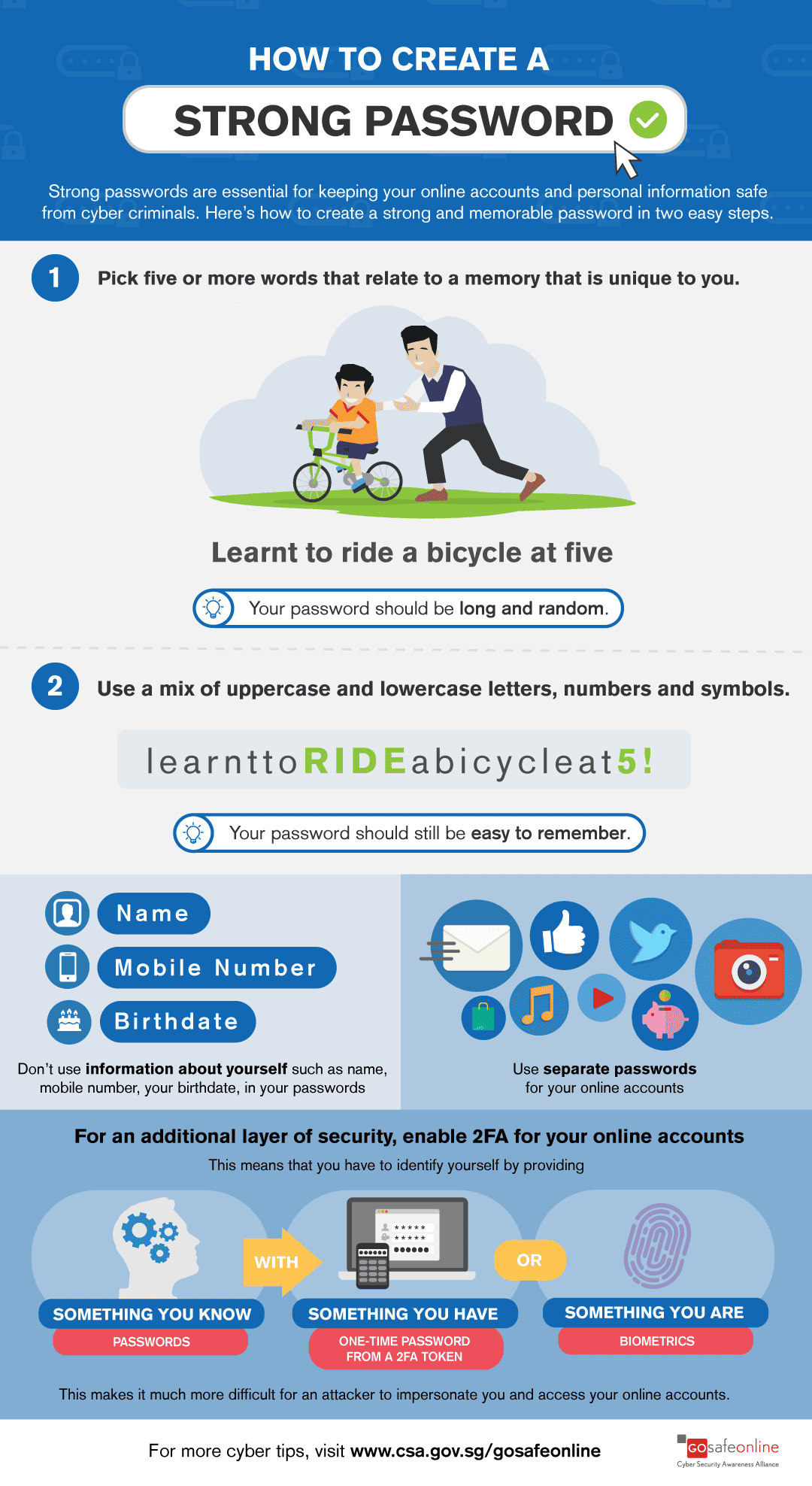
(Image source: csa.gov.sg/gosafeonline)
Incidents like the Florida Virtual School data breach of March 2018 (which resulted in the circulation of a file containing 368,000 student records and 543,000 unique email addresses) don’t just happen because of the ingenuity of the attackers. They’re quite often aided and abetted by the lax password practices of the people and organizations they target.
Adjust Your Social Media Settings
The revelations of the Cambridge Analytica affair and its exposure of the too-cozy relationship between Facebook and its partner agencies and advertisers stresses the need for social media users to maintain their guard.
To reduce the potential for exposure of personal information online, you can start by reviewing your privacy settings and the interaction of your social media account with external applications and agencies on Facebook, LinkedIn, Twitter, and any other platforms on which you’re active.
Functions like time stamps, checking in, geo-tagging, and geo-location should ideally be disabled or used sparingly. This will minimize the potential for outside observers to track your movements and target you for advertising – or something more sinister.
You should also review the information given in your profile, and use discretion when posting comments or items on your news feeds.
Do Look the Gift Horse in the Mouth
Here’s some more parental advice: Don’t take candy from strangers.
Remember it every time you receive an unsolicited email, are tempted by an unbelievable offer, told to “Click here NOW!!”, or encounter anything else online that seems too good to be true – for the chances are it is.
Don’t:
- Respond to urgent-sounding but kind-of-suspicious-looking emails
- Download and open files attached to these kinds of messages
- Click on embedded links messages like these contain,
- Click on active links and buttons – or anything else, for that matter – on suspicious websites and portals
- Give out personal information online unless you’re 100% certain about the identity of the person, business, or service that’s asking for it
Be Careful How You Handle Your Email
Email phishing and social engineering scams look to provoke an immediate emotional response from the message recipient with tempting or threatening proposals. The hope is that the victim will download a file attachment containing malware, click on a link leading to more malicious software or a booby-trapped website, or reveal sensitive personal or business data via a message reply or online form.
Due diligence is required in order to stay safe if you suspect you’re the target of a phishing scam:
- If the message supposedly comes from someone you know, make a call or in-person visit to verify that a message is genuine
- Do an internet search to check out the bona fides of any individual, company, or institution making once in a lifetime offers or serious threats
- Always run a virus/anti-malware scan on any file or document before you download or open it – and after
- Don’t click on embedded links within messages
And remember that these tactics now extend to SMS text messaging, direct messaging on social media, and instant messaging apps.
Close the Doors When You Leave
To avoid retaining numerous stores and instances of your personal information online, make a point of regularly logging out of the accounts and services you normally use. A good password manager application (which you should already have for generating and storing those strong passwords) will help you remember the credentials you need to log back in later.
If you run a home or office wireless network, be sure to require authorized users to log in and out each time they use it – and restrict access only to those people that you know and trust.
Keep Backups of Your Important Data
Regular backups to a removable storage device and/or a cloud storage service from a reputable provider will ensure that you always have usable working copies of your vital documents and files.
Encryption is an important tool for keeping backups and active files safe from intruders and prying eyes. Strong encryption may be a feature offered by your cloud storage provider, so ask about this if it isn’t obvious on the software. Desktop hardware and mobile devices may also be encrypted to protect your stored documents and personal information online. This may be done via the operating system, or using dedicated apps.
Exercise Caution On Public Wi-Fi
Free Wi-Fi hotspots are notorious hangouts for hackers and eavesdroppers, who can hijack unsecured wireless connections to re-route your data to their own systems, or simply snatch packets of information from someone else’s service.
Using a Virtual Private Network (VPN) application or service is your best protection on public Wi-Fi. Aside from this, you should restrict your activities at hotspots to anything that doesn’t require you to give out your personal information. This applies to financial and business transactions, and certain exchanges on social media and online forums.
Minimize Your Personal Information Online
If it’s not there, it can’t be spied on, stolen, or abused. So make the effort to minimize your digital footprint by limiting the number of sites, services, and platforms where you give out personal information online.
Summary:
Protect Personal Information Online
Sounds like a no-brainer, but the age-old parental advice that you should “Never talk to strangers” also applies in the digital world. If an unknown website, email correspondent, or service is asking for sensitive details about you, a straight up refusal should be your instinctive reaction. If there’s a pressing reason to deal with the entity, do a thorough search to check them out before revealing any of your personal information online. Get Smart and Complex with Your Passwords. Security experts continuously stress the importance of maintaining good password habits. Strong passwords consisting of eight or more characters with a mix of numbers, letters, and keyboard symbols are always advised. Don’t: 1. Respond to urgent-sounding but kind-of-suspicious-looking emails 2. Download and open files attached to these kinds of messages 3. Click on embedded links messages like these contain 4. Click on active links and buttons – or anything else, for that matter – on suspicious websites and portals 5. Give out personal information online unless you’re 100% certain about the identity of the person, business, or service that’s asking for it





